33 System Hardening – Windows Firewall
Raechel Ferguson
Windows firewall is a powerful tool for creating firewall rules for an individual computer or when utilized with AD it can be used to develop rules for a server firewall. This activity aims for students to see how AD can utilize group policies and Windows Defender Firewall to create firewall rules for devices connected to the AD server. In addition, this lab also teaches students the differences between inbound and outbound rules and how to create group policies that apply to devices. Finally, this lab will enable learners to see how communications between devices are altered due to the firewall rules created.
Learning Objectives
- Successfully deploy a server firewall to control communications between devices
- Observe how group policies can be applied to devices connected to the server
- Observe how firewall rules alter the communication abilities of devices
Prerequisites
- Chapter 8 – Creating a Windows Server
- Chapter 7 – Creating a Linux Server
- Chapter 16 – Introduction to Routers
Deliverables
- 5 Screenshots:
- Labeled GNS3 workspace
- Router configurations
- Screenshots of:
- Blocked pings to the client 212.10.10.6
- Blocked pings to 212.10.10.6 from the client machines
Resources
- NOTE: Each source will referenced with its corresponding number in superscript (EX: 1 ) at the end of a step
- 1. MSFT WebCast. “Basic Configuration Tasks in Windows Server 2019.” YouTube, January 25, 2019. https://www.youtube.com/watch?v=1nxYJSV7-u8&list=PLUZTRmXEpBy32NP6z_qvVBOTWUzdTZVHt&index=4.
- 2. MSFT WebCast. “How to Join Windows Server 2019 to an Existing Active Directory Domain.” YouTube, February 1, 2019. https://www.youtube.com/watch?v=BEyNwwjo0u4.
- 3. MSFT WebCast. “How to Join Windows Server 2019 to an Existing Active Directory Domain.” YouTube, February 1, 2019. https://www.youtube.com/watch?v=BEyNwwjo0u4.
- 4. Tony Teaches Tech. “How to Block Ping Requests (on Windows, Linux, MAC).” YouTube, January 11, 2022. https://www.youtube.com/watch?v=52T2f8NfN0Y.
Contributors and Testers
- Jungsoo Noh, CIS Student, ERAU-Prescott
- Dante Rocca, CIS Student, ERAU-Prescott
Phase I – Workspace Configuration
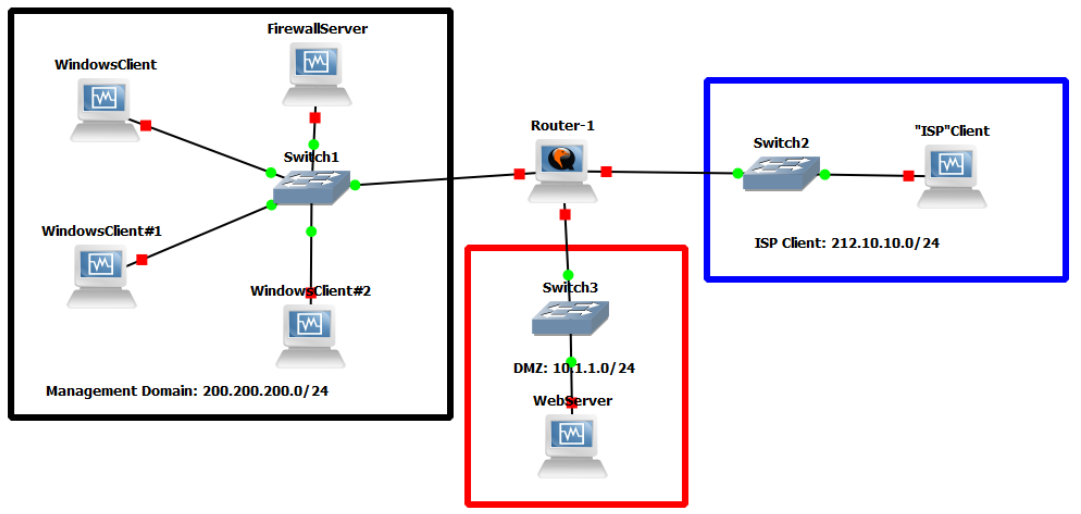
- Open GNS3
- Create a new project: LAB_18
- Add 3 switches and a router to the workplace and name them “Switch 1” through “Switch 3” and keep the router as “Router”
- Add a Windows Client device to the workspace and connect it to switch1
- Add a note above the switch 1 network and write “200.200.200.1/24”
- Switch to VirtualBox and right click on the Windows 10 Client machine and select the option to clone the VM
- Select Expert Mode and then the Linked Clone option
- Clone the Windows Client machine a total of 3 times (4 VMs total)
- Add those cloned machines in GNS3
- Connect only two of the new cloned machines into the workspace and connect them to Switch 1
- Take the last cloned machine and connect it to Switch 2
- Add a Windows Server machine to the Workspace and connect it to Switch 1 and then name it Firewall Server
- Connect Switch 1, 2, and 3 to the Router, with Switch 1 being on ethernet 0, switch 2 being on ethernet 1, and switch 3 being on ethernet 2
- Turn on the Firewall server and one of the client machines connected to switch 1.
NOTE: Turing on 2 additional machines takes up a lot of your host computer’s memory and power so limit the number of total machines on to 3
- Log into both the server and client machine
Phase II – Server and client configuration
- Once logged into the server and client machines, access the server first
- Once in the server machine click on server manager and click on Local Server 1
- Left-click on the ethernet option in the middle of the screen, this is under NIC Teaming and above Operating System Version 1
- Once the ethernet option screen has appeared right click on the ethernet option making sure it is enabled and select Properties 1
- In the new window uncheck the IPv6 option, then click on the IPv4 option and click on the properties button 1
- On the IPv4 Properties screen click on Use the following IP address, enter “200.200.200.6” as the IP address, enter “255.255.255.0” as the subnet mask, and then enter “200.200.200.1” as the Default gateway 1
- In the Preferred DNS server box enter an IP address of “200.200.200.6,” leave the other DNS box empty 1
- Click ok
- Add client machine to server domain
NOTE: Before this step make sure one of the adapters on both the client and server machines is set to Generic Driver, allow all, and make sure Cable Connected is checked. (This makes sure the client and server can see each other). Keep the other 3 adapters to Not Attached at this time for both machines.
- Once logged on to the client machine click on the magnifying glass icon in the lower left-hand corner. Enter the word cmd and press enter to access the command line
- Once the command line has popped up enter the command:
ncpa.cpl
You should see a window pop up
- Right-click on one of the ethernet options and select Properties 2
- In properties click on the IPv4 option and select the properties button. Once in IPv4 select the Use the following IP address option 2
- In the IP address spot enter 200.200.200.7, click on subnet mask and make sure the information is 255.255.255.0 (If not enter that address). Enter a default gateway of 200.200.200.1 2
- Below select the Use the following DNS server address option. Enter a DNS server address of 200.200.200.6 (Server DNS address), leave the other DNS box empty. Select the ok button and close all opened windows 2
- Click on the magnifying glass icon in the lower left-hand corner. Search for Control Panel and hit enter 2
- Click System and Security, then click on System 2
- Under About click on Rename this PC (Advanced) 2
- In the Computer Name tab click on the Change option. In the Member of section click on Domain and type the name of the domain of your server (in local server if you forget). Click ok 2
- Log into your server with the username Administrator and the password to your server machine 2
- Once you have successfully joined the domain restart the client machine and log back into the machine
- Switch to the server machine and open the command line and ping the client machine to ensure the two devices can speak to each other
- Adding the other 2 client machine clones connect to switch one to the server domain
- Follow steps 2.1 to 2.13 for each of the two clone machines, only select a different main IP address for each clone
- One clone will have the IP address of 200.200.200.8 and the other clone machines so as to not get the cloned clients and the main client machine confused
- Ensure all the devices can see and speak to each other
- Configure the router
- In GNS3 start and login to the router
- Assign each interface on the router an IP address
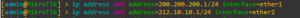
- For the first connection enter the following:
ip address add address=200.200.200.1/24 interface=ether1
- Lastly, enter: (Figure 2)
ip address add address=212.10.10.1/24 interface=ether2
Phase III – Set-up firewall rules in active directory
- Configure firewall profiles
- In the server machine click on server manager and then local server 3
- In the local server click on the Tools in the upper right-hand corner. From tools click on Active Directory Users and Computers 3
- In the Active Directory Users and Computers window right click on the domain name of your server, click new and then click Organizational Unit. Add the name of your chosen OU (TestOU in the example) and then click OK 3
- Left click on the domain name of your server. Under the computers tab, drag and drop all the clients connected to the server domain and drop them into the new OU. If you get a popup just select yes 3
- Go back into the tools tab and click on Group Policy Management 3
- Expand the Forest and then expand the Domains. Expand your domain 3
- Expand Group Policy Objects and right click on it, select the new option to create a new object. Name this object Firewall Rules 1 for easy identification and click ok 3
- Select the Firewall Rules 1 object under Group Policy Objects and right click on it and select the Edit option 3
- Under Computer Configuration, expand Policies and then expand Windows Settings and then Security Settings and then Windows Defender Firewall with Advanced Security. Click on the Windows Defender with Advanced Security – LDAP… option 3
- On the right side of the screen select the green text that states Windows Defender Firewall Properties 3
- In the Domain Profile tab of the new wizard set the firewall state to ON (recommended) then set the Inbound Connections to Block (Default). Set the Outbound Connections to Allow (Default) 3
- Set the same options in the Private and Public tabs 3
- Once all the rules are set select the Apply option and then the OK option in the Window Defender Firewall with Advanced Security wizard 3
- Close the Group Policy Editor Window 3
- Click on the OU you created and then right click on it and select Link and Existing GPO. Select the Firewall Rules GPO that you created and click OK
- In your client machines update the group policy by entering the following command: 3
gpupdate /force
- Connect to ISP client
- In GNS3 turn on the separate client connected to switch 2
- Configure the client to have the IP address of “212.10.10.6” with a subnet mask of “255.255.255.0” and a default gateway of “212.10.10.1” Leave DNS as the option that the machine supplied or 8.8.8.8
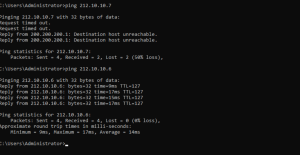
- Try pinging the ISP client from the firewall server. The pings should go through since there is no firewall rule blocking the connection (Figure 3)
Phase IV – Configure firewall rules to clock outbound and inbound pings
- In the Firewall server machine right click on Tools in the local server page and select Group Policy Management 4
- Expand Group Policy Objects and right-click on it, select the new option to create a new object. Name this object Firewall Rules 2 for easy identification and click ok 4
- Select the newly created object and right click on it and select the Edit option 4
- Expand Policies and then expand Windows Settings and then Security Settings and then Windows Defender Firewall with Advanced Security then select Windows Defender Firewall with Advanced Security option 4
- Once inside the Windows Firewall configuration wizard, select the green text that states Inbound Rules 4
- In the Inbound rules section, click on the text that states New Rule on the right-hand side of the screen
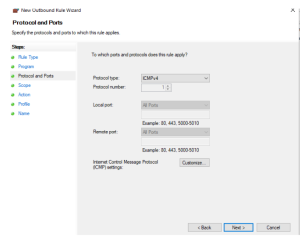
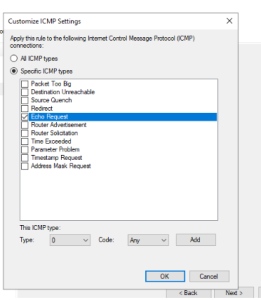
- Select the Custom option and click next then click next again, then in the Protocol and Ports screen select ICMPv4 from the protocol type drop down. Then click on the customize option towards the bottom, click specific ICMP types option and then tick the Echo Requests option, then click ok and next 4
- In the scope screen enter the IP address of 212.10.10.6 to the remote IP address box by clicking on add and entering the IP address. Click ok after entering the IP address and then click next 4
- In the action screen click Block the connection and then click on next. In the profile screen only click the Domain option and then click next. Name the rule something along the lines of “Block Pings from 212.10.10.6” Then click on the finish option 4
- In your client machines update the group policy by entering the following command:
gpupdate /force
- Try and ping the client machines from 212.10.10.6, the pings are now blocked due to the newly created firewall rules.
- Block outbound pings
- In the local server screen right click on the tools option and then select the Expand Group Policy Objects option 4
- Click on the OU you created then right click on Firewall Rules and select the edit option 4
- Expand Policies and then expand Windows Settings and then Security Settings and then Windows Defender Firewall with Advanced Security then select Windows Defender Firewall with Advanced Security option 4
- Once inside the Windows Firewall configuration wizard, select the green text that states Outbound Rules
- In the Inbound rules section, click on the text that states New Rule on the right-hand side of the screen 4
- Select the Custom option and click next then click next again, then in the Protocol and Ports screen select ICMPv4 from the protocol type drop down. (Figure 4) Then click on the customize option towards the bottom, click specific ICMP types option and then tick the Echo Requests option then click ok and then next 4 (Figure 5)
- In the scope screen enter the IP address of 212.10.10.6 to the remote IP address box by clicking on add and entering the IP address. Click ok after entering the IP address and then click next 4
- In the action screen click Block the connection and then click on next. In the profile screen only click the Domain option and then click next. Name the rule something along the lines of “Block pings from 212.10.10.6” Then click on the finish option 4
- In your client machines update the group policy by using the following command:
gpupdate /force
- Try and ping 212.10.10.6 from the client machines, the pings are now blocked due to the newly created firewall rules
- The above two rules show how a firewall can block pings from coming in and it can block users within a domain from pinging a client on another domain and IP range.
End of Lab
Deliverables
5 screenshots are needed to receive credit for this exercise:
- Labeled GNS3 workspace
- Router configurations
- Screenshots of:
- Blocked pings to the client 212.10.10.6
- Blocked pings to 212.10.10.6 from the client machines
Homeworks
- Assignment 1 – Firewall rules recap
- Create another client device clone
- Add that clone to the management domain network & assign it an IP
- Connect the clone to the server & update its group policy
- Try and ping the devices from the above steps
- Screenshot the blocked pings from the newly added clone
- Assignment 2 – Research a firewall rule
- Take some time to research recommend firewall rules (use trusted sources)
- Try to implement said rule that was found
- Screenshot the rule either working or not working
- Write a small (1 -2 paragraph) response on what rule you chose, why you chose that rule, and whether was it able to be implemented
- In your response, ALL sources should be listed
Figures for Printed Version